As an Android user, you may wonder one day how to secure rooted Android from security threats. Android is the most popular mobile operating system in the world, with over 2.5 billion active devices. However, Android devices are vulnerable to security threats and rooted Android devices are even more susceptible to attacks.
Rooted Android devices are those that have been modified to gain administrative privileges or access to the root file system. While rooting can provide users with more control over their devices, it can also make them more vulnerable to security threats. In this article, we’ll take a closer look at how to secure rooted Android devices from security threats.
Read also: How to make your Android always online from WhatsApp and FB Messenger
Read also: How to recover deleted files on Android phone
The steps required to secure rooted Android from security threats
1. Install a trusted antivirus app
One of the most important steps to secure rooted Android from security threats is to install a trusted antivirus app. Antivirus apps can detect and remove malware, viruses, and other security threats. Some of the best antivirus apps for Android include Avast Mobile Security, Norton Mobile Security, and Kaspersky Mobile Antivirus.
2. Keep your device updated
To secure rooted Android from security threats you may need to keep your rooted Android device updated is crucial for security. Android updates often include security patches and bug fixes that can protect your device from security threats. It’s important to regularly check for updates and install them as soon as they become available.
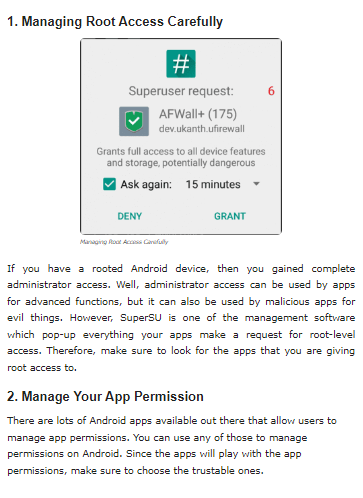
3. Use a firewall
A firewall can help protect your device from unauthorized access and malicious traffic. There are several firewall apps available for rooted Android devices, including AFWall+ and NoRoot Firewall. These apps allow users to control which apps have access to the internet and can block incoming connections.
4. Disable root access for certain apps
Root access can give apps more control over your device, but it can also make them more vulnerable to security threats. It’s important to disable root access for certain apps that don’t require it. This can be done using a root management app, such as SuperSU or Magisk.
5. Use secure passwords
Using a strong and unique password is crucial for securing your rooted Android device. Avoid using common passwords or passwords that are easy to guess. It’s also a good idea to use a password manager app, such as LastPass or 1Password, to generate and store secure passwords.
6. Enable two-factor authentication
Two-factor authentication adds an extra layer of security to your device by requiring a code or token in addition to a password. This can help prevent unauthorized access to your device and sensitive information. Many apps and services, such as Google and Facebook, offer two-factor authentication options.
7. Be cautious when downloading apps
One of the most common ways for security threats to enter a rooted Android device is through malicious apps. It’s important to only download apps from trusted sources, such as the Google Play Store. Be cautious of apps that request excessive permissions or that seem too good to be true.
8. Use encryption
Encrypting your data can help protect it from unauthorized access. Many rooted Android devices come with encryption tools built in, such as Android’s built-in encryption feature. It’s important to use encryption for sensitive data, such as passwords, financial information, and personal documents.
In conclusion, to secure rooted Android from security threats requires a combination of steps, including installing a trusted antivirus app, keeping the device updated, using a firewall, disabling root access for certain apps, using secure passwords, enabling two-factor authentication, being cautious when downloading apps, and using encryption. By following these steps, users can ensure their rooted Android device is secure and protected from security threats.


