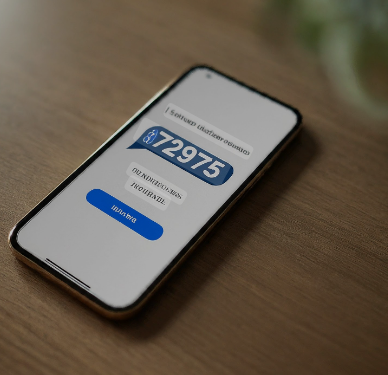
An unexpected text message from a 5-digit number can be unsettling, especially when it mentions a financial account like PayPal. If you’ve received a text from the short code 72975, you are not alone. This number has been the subject of widespread confusion, concern, and online discussion across the United States. This comprehensive report will serve as the definitive guide to understanding the 72975 short code. We will dissect its legitimacy, explain its connection to PayPal, detail the mechanics of associated scams, and provide a complete action plan to secure your accounts and protect your financial identity.
Decoding the 72975 Text Message: Is It a Scam or Is It Legit?
To address the most pressing question directly: the short code 72975 is an official and legitimate number used by PayPal for sending text messages. Multiple official PayPal help center documents confirm that when two-factor authentication is enabled on an account, login confirmation texts will come from one of their designated numbers, explicitly listing both 729725 and 72975. This is further corroborated by third-party cybersecurity experts, such as Luis Corrons of Norton, who identifies 72975 (PAYPL) as an official short code for the company.
The Primary Purpose of 72975: Two-Factor Authentication
The main function of the 72975 short code is to facilitate PayPal’s two-step verification system, more commonly known as two-factor authentication (2FA). This is an essential security feature that adds an extra layer of protection to your account. When 2FA is active, any attempt to log in requires not only your password but also a temporary, single-use security code. PayPal sends this code via SMS from numbers like 72975 to the phone number registered to the account, ensuring that only the person with physical access to the phone can complete the login.
The Unsolicited Code Problem: A Legitimate Warning Sign
The most common source of alarm for consumers is receiving a security code from 72975 when they have not personally tried to log into their PayPal account. It is crucial to understand what this event signifies. The text message itself is not a scam; rather, it is a legitimate security alert triggered by a potentially fraudulent action.
Receiving an unrequested 2FA code is a strong indication that someone else has your PayPal password and is actively trying to access your account. The 2FA system is functioning exactly as it should: it has successfully blocked the unauthorized login attempt because the intruder does not have the code that was sent to your phone. Therefore, the text message should not be dismissed as spam. It is a critical warning that your password has been compromised and immediate action is required to secure your account. The focus should shift from questioning the legitimacy of the text to understanding why a real security alert was triggered without your knowledge.
The Legitimacy Paradox: Why So Much Confusion Surrounds 72975?
Despite official confirmation of its legitimacy, a significant amount of confusion and suspicion persists around the 72975 short code. This “legitimacy paradox” is not unfounded; it stems from a combination of historical errors, inconsistent user experiences, and conflicting information that has created a trust deficit actively exploited by scammers.
The “PayPal Serivices” Typo: A Major Red Flag
One of the primary drivers of the “scam” narrative is a widely reported historical registration error. Multiple online forums and user discussions point to short code directories that once listed 72975 as being registered to “PayPal Serivices,” with a conspicuous misspelling of “Services”. For any security-conscious user, such a typo is an immediate and significant red flag, understandably leading many to conclude the number is fraudulent. While records show the SMS short code 72975 was officially registered on March 25, 2020, for “PayPal Services,” the persistence of this reported typo in various directories has done lasting damage to the number’s credibility.
Conflicting User Experiences and Support Information
The confusion is compounded by inconsistent experiences reported by PayPal users themselves. Numerous threads on platforms like Reddit contain contradictory anecdotes:
- Contradictory Support: Some users claim they have contacted PayPal customer service directly and were told that 72975 is not a legitimate number used by the company. This conflicting information from official channels is a major source of uncertainty.
- Website vs. App Discrepancy: Other users have conducted their own tests and discovered a pattern. When they intentionally request a 2FA code from the PayPal website on a computer, the text arrives from 72975. However, when requesting a code through the mobile app, it often comes from the more widely recognized 6-digit short code, 729725. This suggests an internal system difference that is not clearly communicated to the public.
- Mixed Messages: To further complicate matters, some individuals report receiving both legitimate and seemingly fraudulent messages from both numbers, making it nearly impossible for the average person to establish a clear rule of thumb.
This combination of a historical registration error, inconsistent information from customer support, and differing system behaviors creates a “trust vacuum.” Scammers are well aware of this confusion and can weaponize it. For example, a fraudster could trigger a real 2FA code from 72975, knowing the user might be suspicious and ignore it. The scammer could then follow up with a phishing email or a spoofed phone call, pretending to be PayPal support “investigating the suspicious text,” and use this manufactured concern to trick the user into revealing personal information. In this way, the public’s confusion becomes a powerful tool for social engineering.
The Technical Possibility of Spoofing
Finally, it is technically possible for criminals to “spoof” a phone number, making a text or call appear to come from a source it did not. While this is more difficult to achieve with SMS short codes compared to standard 10-digit phone numbers, the possibility cannot be entirely dismissed. However, the far more probable scenario for an unsolicited 2FA code from 72975 is a legitimate text triggered by a fraudulent login attempt, not a spoofed message.
The 72975 PayPal “Smishing” Scam: How It Really Works
Understanding that 72975 is a real PayPal number is only the first step. The true danger lies in how criminals leverage the alerts from this number as part of broader “smishing” (SMS phishing) campaigns designed to steal your money and identity.
The Two-Stage Attack
The scam often unfolds in two distinct stages, preying on the user’s reaction to the initial, legitimate text alert.
Stage 1: The Password Breach and 2FA Trigger The process begins when a scammer obtains your PayPal username and password, often through a previous data breach, malware, or a different phishing attack. They then attempt to log into your account. This action triggers PayPal’s security system to send a legitimate 2FA code from 72975 to your phone. This is the unsolicited text you receive. The scammer is now stuck, unable to proceed without that code.
Stage 2: Exploiting the Alert The scammer’s goal now shifts to either tricking you into providing the code or creating a separate opportunity while you are distracted or confused. A powerful, real-world example from a Reddit user illustrates this perfectly:
- The user received multiple unsolicited security codes from 72975.
- Wisely, they did not click any links or reply. Instead, they logged into their PayPal account directly through their computer’s web browser.
- Upon reviewing their account, they discovered a fraudulent “Cash request” for $547.93 pending from a scammer.
In this case, the scammer, after failing to log in, used a different PayPal feature—requesting money—hoping the user might approve it by mistake, especially if they were confused by the security alerts. The 72975 text was the warning sign that prompted the user to check their account and uncover the secondary attack.
Common Phishing Tactics to Watch For
Whether initiated by a 72975 alert or arriving out of the blue, PayPal-themed phishing attacks share common traits. Being able to recognize these red flags is your best defense.
- Urgent and Threatening Language: Scams often create a false sense of urgency, using phrases like “unusual activity detected,” “account has been restricted,” or “your account will be suspended” to rush you into making a mistake.
- Suspicious Links: Scammers will include links that direct you to a “spoofed” website—a pixel-perfect clone of the real PayPal login page. Hovering over the link on a computer or long-pressing it on a mobile device will reveal the true URL, which will not be
paypal.com. - Generic Greetings: Legitimate PayPal communications will always address you by your full name as it appears on your account. Phishing messages frequently use impersonal greetings like “Dear Customer,” “Dear User,” or “Hello, PayPal member”.
- Requests for Sensitive Information: PayPal will never ask you to provide your password, full credit card number, or answers to your security questions in an email or text message. Any message requesting this information is a scam.
- Spelling and Grammar Errors: While scammers are becoming more sophisticated, many phishing messages still contain obvious typos and grammatical mistakes.
To help you quickly distinguish between authentic and fraudulent communications, consult the following comparison table.
Your Action Plan: What to Do If You Receive a Suspicious Text from 72975
Receiving an unsolicited security code can be alarming, but it is a solvable problem. By following a clear, methodical action plan, you can transform a moment of vulnerability into an opportunity to significantly enhance your account security.
Step-by-Step Guide for Unsolicited Codes
If you receive a security code text from 72975 that you did not request, follow these steps immediately:
- Do NOT Panic and Do NOT Interact with the Message: Your first instinct should be to remain calm. Do not click on any links in the text. Do not call any phone numbers provided. Do not reply with the security code or any personal information. While you can typically reply “STOP” to a short code to unsubscribe from that specific messaging campaign, this will not resolve the underlying security risk that your password has been compromised.
- Secure Your PayPal Account Immediately: Open a new, clean browser window or use the official PayPal mobile app. Manually type
paypal.cominto the address bar and log in to your account. Do not use a search engine to find the login page, as this can sometimes lead to sponsored scam links. Once logged in:- Change your password. Create a new password that is long (at least 12-16 characters), complex (using a mix of upper and lowercase letters, numbers, and symbols), and unique (not used for any other account).
- Update your security questions. Choose questions and answers that are not easily guessed or found on your social media profiles.
- Review Your Account Activity: Navigate to your account’s activity and login history sections. Carefully review all recent transactions, login locations and times, and any pending money requests. Report any unauthorized activity you find directly to PayPal through their Resolution Center.
- Enable a More Secure Form of 2FA: SMS-based 2FA is a good first step, but it is vulnerable to attacks like SIM swapping. A more secure method is to use an authenticator app (such as Google Authenticator or Microsoft Authenticator). These apps generate time-sensitive codes directly on your device, independent of your mobile number. You can enable this feature in your PayPal security settings. Note that some PayPal documentation suggests that if you disable SMS 2FA, you may not be able to re-enable it, further encouraging the switch to a more secure authenticator app.
- Report the Incident: Forward the suspicious text message (if possible) or a description of the event to PayPal’s security team at
[email protected]. This helps them track and combat ongoing scam campaigns.
Emergency Checklist: If You’ve Already Clicked a Link or Responded
If you fear you may have already fallen for a phishing scam by clicking a link and entering your information, you must act with greater urgency. Follow this emergency checklist to mitigate the damage.
| Step | Action | Why It’s Critical |
| 1 | Disconnect from the Internet | Immediately disconnect the compromised device (computer or phone) from Wi-Fi or cellular data. This can sever a scammer’s connection and prevent the installation of additional malware or the exfiltration of more data. |
| 2 | Change Passwords Immediately | Using a separate, trusted device, change the password for your PayPal account first. Then, change the password for your associated email account. Finally, change the password for any other online account that used the same or a similar password. |
| 3 | Contact Your Financial Institutions | Call the fraud department of your bank and any credit card companies whose information is linked to your PayPal account. Report the potential fraud, explain that your account was compromised, and ask them to monitor for and block any unauthorized charges. |
| 4 | Run a Full Malware Scan | Use reputable antivirus and anti-malware software to perform a full scan of the device you used to click the link. This will help detect and remove any malicious software that may have been installed. |
| 5 | Place a Fraud Alert on Your Credit Files | Contact one of the three major credit bureaus (Equifax, Experian, or TransUnion) to place an initial fraud alert on your credit file. The one you contact is required to notify the other two. This alert makes it harder for a scammer to open new accounts in your name. |
Beyond 72975: A Guide to Reporting All Unwanted SMS Messages and Robocalls
The frustration caused by the 72975 text is part of a much larger problem of unwanted and illegal spam texts and robocalls. Many consumers feel powerless against this digital deluge, but there are official channels through which you can and should report these intrusions. Your reports provide valuable data that helps law enforcement and regulatory agencies track down and penalize offenders.
Reporting to U.S. Government Agencies
Two primary federal agencies are responsible for handling consumer complaints about unwanted communications.
- The Federal Trade Commission (FTC): The FTC manages the National Do Not Call Registry. While this registry is designed to stop sales calls from legitimate companies, it is also the primary tool for reporting all unwanted calls, including illegal robocalls and scam calls.
- How to Report: You can file a complaint online at
DoNotCall.govor by calling 1-888-382-1222. - What to Include: Be prepared to provide your phone number, the number that appeared on your caller ID, and the date and time of the call.
- Why It Matters: The FTC uses this complaint data to identify trends, conduct investigations, and build cases against scammers. The phone numbers you report are also shared daily with telecommunications carriers to help improve call-blocking and labeling technologies.
- How to Report: You can file a complaint online at
- The Federal Communications Commission (FCC): The FCC sets and enforces the rules that govern telecommunications, including the Telephone Consumer Protection Act (TCPA). Unwanted robocalls and texts are the agency’s top consumer complaint.
- How to Report: File a complaint through the FCC Consumer Complaint Center at
fcc.gov/complaints. - Why It Matters: Like the FTC, the FCC uses complaint data to inform its enforcement actions and policy decisions aimed at curbing the tide of illegal calls and texts.
- How to Report: File a complaint through the FCC Consumer Complaint Center at
Reporting Spam Directly from Your Phone
Modern smartphones make it easy to report spam directly from your messaging app. This action helps your mobile carrier identify and block spam sources.
- On iOS (iPhone): Open the suspicious message, tap the sender’s profile icon at the top, tap “Info,” and then select “Report Junk.”
- On Android: The process varies slightly by manufacturer, but generally involves opening the message, tapping the three-dot menu icon, and selecting “Details” and then “Block & report spam”.
In addition to reporting, you should also block the number to prevent further messages from that specific source. While scammers frequently change numbers, blocking known offenders can provide some immediate relief.
When a Scam Becomes a Crisis: A Guide to Identity Theft Protection
A compromised PayPal password is more than just an inconvenience; it can be the first thread that unravels your entire financial identity. Criminals who have your password for one service will systematically try it on other platforms—your email, banking, and social media accounts—a technique known as credential stuffing. This is why a single security alert can be a precursor to full-blown identity theft. In this high-stakes environment, proactive monitoring services have become an essential tool for financial security.
What are Identity Theft Protection Services?
Identity theft protection services are comprehensive monitoring solutions that act as a digital watchdog for your personal information. They go far beyond what an individual can do on their own by continuously scanning a vast array of sources for any sign that your data is being misused. Key features typically include:
- Dark Web Monitoring: Scanning illicit marketplaces and forums on the dark web for your stolen credentials, Social Security number (SSN), and credit card numbers.
- Credit Monitoring: Alerting you to changes in your credit reports from one or all three major credit bureaus (Equifax, Experian, and TransUnion), such as new account openings or hard inquiries.
- SSN and Identity Monitoring: Notifying you if your SSN is found in a data breach or used to open new accounts.
- Financial Account Monitoring: Alerting you to high-risk transactions or takeover attempts on your linked bank and investment accounts.
- Identity Restoration and Insurance: Providing expert assistance to help you recover your identity after a theft and offering insurance policies to cover stolen funds and associated costs.
Review of Top Identity Theft Protection Services
The market for identity theft protection is crowded, but several services consistently stand out for their features, reliability, and value.
- Aura: Frequently cited as the “Best Overall” service, Aura offers an all-in-one solution that combines robust identity and three-bureau credit monitoring with a full suite of cybersecurity tools, including a VPN, antivirus software, and a password manager. Its family plans are particularly notable for covering up to five adults and unlimited children, with insurance coverage reaching up to $5 million.
- LifeLock by Norton: As one of the most established names in the industry, LifeLock is praised for its deep integration with Norton’s award-winning digital security products. It offers extensive monitoring features, including home title and social media alerts, and provides some of the highest insurance coverage amounts on the market, up to $3 million for certain plans.
- Identity Guard: Often recommended as a “Best Budget Value,” Identity Guard leverages IBM’s Watson AI for its monitoring and alert systems. It provides a strong core set of identity protection features at a more accessible price point, making it a great option for individuals seeking solid protection without the cost of a full cybersecurity suite.
- IDShield: This service distinguishes itself with its focus on identity restoration and legal support. In the event of identity theft, IDShield provides access to licensed private investigators and offers a restoration guarantee. This makes it an excellent choice for those who prioritize expert-led recovery assistance.
Comparison of Top Identity Theft Protection Services
For consumers who have experienced a security scare, choosing the right protection service is a critical next step. The following table provides a high-level comparison to aid in this decision, targeting the high-intent search for “best identity theft protection services.”
Your Consumer Rights: Legal and Financial Recourse for Scam Victims
Falling victim to a scam can be a devastating experience, both financially and emotionally. It is important to know that you are not powerless. A framework of consumer protection laws and agencies exists to help you report the crime, mitigate the damage, and seek recourse. Targeting keywords like “legal advice for online scam victims” is crucial for connecting users in crisis with the right information.
Immediate Steps After Financial Loss
If a scam has resulted in a direct financial loss, time is of the essence.
- Contact Your Bank or Credit Card Issuer: Immediately call the fraud department of the financial institution involved. Report the unauthorized transactions and request a chargeback or reversal. Federal law provides protections for consumers against fraudulent charges, but prompt reporting is key.
- Report to Money Transfer Services: If you sent money via a wire service, contact them immediately. Provide the details of the fraudulent transaction and request that the transfer be stopped or reversed.
- MoneyGram: 1-800-926-9400
- Western Union: 1-800-448-1492
Reporting the Crime to Law Enforcement
Financial scams are crimes and should be reported as such. Official reports create a paper trail that is essential for investigation and can be required by banks or insurance companies.
- Local Police Department: File a report with your local police or sheriff’s office. Obtain a copy of the police report for your records.
- FBI’s Internet Crime Complaint Center (IC3): For any crime involving the internet, from phishing to financial fraud, the IC3 is the central reporting hub for the FBI. File a detailed complaint at
ic3.gov. This data is crucial for the FBI to track and combat large-scale cybercrime operations.
Filing Complaints with Consumer Protection Agencies
In addition to law enforcement, several federal agencies are dedicated to consumer protection.
- Federal Trade Commission (FTC): The FTC is the nation’s primary consumer protection agency. Report all types of fraud and scams at
ReportFraud.ftc.gov. While the FTC does not resolve individual cases, your report is entered into a secure database used by thousands of law enforcement officials to build cases. - Consumer Financial Protection Bureau (CFPB): If your issue involves a financial product or service, such as a bank account, credit card, or money transfer, you can also file a complaint with the CFPB. The agency can help facilitate a response from the company involved.
For cases involving significant financial loss, it may be necessary to consult with an attorney to explore options for civil litigation to recover funds.
The Technology Behind the Text: Understanding the U.S. Short Code System
To fully demystify the 72975 number, it helps to understand the regulated system that governs all SMS short codes in the United States. These are not just random numbers; they are part of a highly structured and managed ecosystem designed for business-to-consumer communication.
What is an SMS Short Code?
An SMS short code is a special 5- or 6-digit phone number specifically designed for high-throughput text messaging, also known as Application-to-Person (A2P) messaging. Businesses use them for marketing alerts, appointment reminders, 2FA codes, and other automated communications.
The Governing Bodies of the Short Code System
The short code system in the U.S. is not a free-for-all. It is administered by several key organizations to ensure reliability and protect consumers.
- CTIA – The Wireless Association: The CTIA is the trade association representing the U.S. wireless communications industry. It oversees the entire Common Short Code program, setting the best practices and guidelines that all participants must follow.
- Common Short Code Administration (CSCA): The CSCA is the body that directly manages and administers the registry of short codes. It ensures that each code is unique and that the companies using them comply with industry standards to prevent spam and abuse.
- The U.S. Short Code Registry: This is the official, centralized database of all available and leased short codes. The registry is managed on behalf of the CTIA by a service provider called iconectiv. Businesses and organizations can visit the official registry website at
usshortcodes.comto search for available codes.
The Leasing and Vetting Process
Businesses do not own short codes; they lease them for specific periods, typically ranging from three to twelve months. Before a lease is granted, the applicant must undergo a comprehensive vetting process. This process verifies that the company is a legitimate entity and requires a detailed description of the “use case”—how the short code will be used for messaging. This system is designed to protect consumers from unwanted messages and fraudulent campaigns.
This regulated framework provides the ultimate context for the 72975 issue. It shows that there is a formal system in place, and while errors like the “PayPal Serivices” typo can occur, the number itself is part of an official, managed registry. For consumers who wish to verify information directly, the U.S. Short Code Customer Support Team can be reached at 1-866-623-2272 or [email protected].
Conclusion: From Confusion to Empowerment
The journey that begins with a single, confusing text message from 72975 often leads to a broader awareness of personal cybersecurity. While this short code is a legitimate communication channel for PayPal, an unsolicited message from it serves as a critical and timely warning: your account credentials may be compromised.
The key takeaway is to treat such an alert not as a scam in itself, but as a call to action. By immediately securing your PayPal account, upgrading your security settings to more robust methods like authenticator apps, and remaining vigilant for secondary phishing attempts, you can turn a potential threat into a significant security upgrade.
Furthermore, this single event underscores the pervasive risks of the modern digital landscape. The confusion surrounding the 72975 number highlights the sophisticated ways in which scammers exploit uncertainty. This makes a compelling case for leveraging professional identity theft protection and credit monitoring services. These services provide a crucial safety net, offering continuous monitoring and expert restoration support that is essential for navigating an environment where data breaches and phishing attacks are a constant threat. By understanding the risks and utilizing the tools and resources available—from reporting scams to the FTC and FCC to investing in proactive protection—consumers can move from a position of uncertainty and fear to one of empowerment and control over their financial security.


